NHS Smartcard Support in Linux
A long story short: an Extranet project needs support for smartcard authentication. Given the end-users are in the NHS, the NHS Smartcard seems like the ideal platform. But there are pitfalls.
Problems:
- You can't get an NHS smartcard without being in the NHS, or someone in the NHS signing you up.
- You can't get an NHS smartcard without signing an agreement that you will not tamper with the card, its data, or anything else.
These problems were easily solved by an NHS employee "borrowing" a blank, unissued card.
Problems:
- The smartcard is manufactured by Gemplus.
- The smartcard is a GemSAFE GPK variant.
- Gemplus have a sales brochure for the GemSAFE SDK.
- The budget for this project is well defined: it is zero.
These problems can be more-or-less solved by doing a little reverse engineering work. Again, to cut the long story short, here is the solution!
Solution
First, you need OpenSC v0.10 or higher. Debian Sarge ships with v0.9.6. At the time, it made the most sense for me to backport the GemSAFE driver, src/libopensc/pkcs15-gemsafe.c, from v0.10.0-beta1 to v0.9.6. The result of this can be found in opensc_0.9.6-1+gemsafe-0.10.0-beta1-1.tar.gz, and are also available compiled for Debian Sarge on i386 and amd64 from:
deb http://deb.faelix.net/debian/faelix sarge faelix deb-src http://deb.faelix.net/debian/faelix sarge faelix
After that, it was a case of editing /etc/opensc/opensc.conf:
app default {
# ... elided for brevity ...
reader_drivers = pcsc;
card_drivers = gpk, flex, internal;
# ... elided for brevity ...
framework pkcs15 {
use_caching = true;
enable_pkcs15_emulation = yes;
try_emulation_first = yes;
enable_builtin_emulation = yes;
builtin_emulators = gemsafe;
emulate gemsafe {
atr = 3B:A7:00:40:18:80:65:A2:09:01:03:52;
}
}
# ... elided for brevity ...
}
Insert NHS smartcard and test:
maz@paradigmshift:~$ opensc-tool -a 3B A7 00 40 18 80 65 A2 09 01 03 52 ;..@..e....R maz@paradigmshift:~$ opensc-tool -n Gemplus GPK driver
Reverse-engineering complete, I filled in the application for an NHS smartcard. Then I was able to finally test the certificates were available:
maz@paradigmshift:~$ pkcs15-tool -r 01 -----BEGIN CERTIFICATE----- MIIDejCCAmKgAwIBAgIEQMXL4zANBgkqhkiG9w0BAQUFADAyMQwwCgYDVQQKEwNu aHMxCzAJBgNVBAsTAkNBMRUwEwYDVQQDEwxOSFMgTGV2ZWwgMUEwHhcNMDUxMTIy MTAwNTEwWhcNMDcxMTIyMTAzNTEwWjA2MQwwCgYDVQQKDANuaHMxDzANBgNVBAsM ...snip... Mm04gVEkFaKHzFy0C9duQdDXeYAmlf3KTq6cFgqacnZoIa/++G4ZahfpzFM6otH4 sHEUQ8+Z6iM6W77p2NfAVUBdlsbA5rSn8SgC8tvd069cqMUw76IpfMhw73uHnsx1 BYvn+pq34fILde7i8ti11e6ppgeQ3ru0GTbj/dBz -----END CERTIFICATE-----
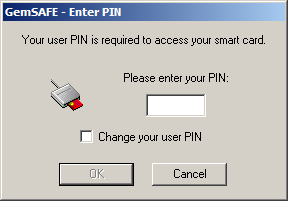
Use in Windows
The NHS has purchased lots of GemSAFE software for Microsoft
platforms, so use is a breeze. Setup your HTTPS (or other) server
appropriately, and Internet Exploder should greet you with a
certificate prompt, and then PIN verification box.
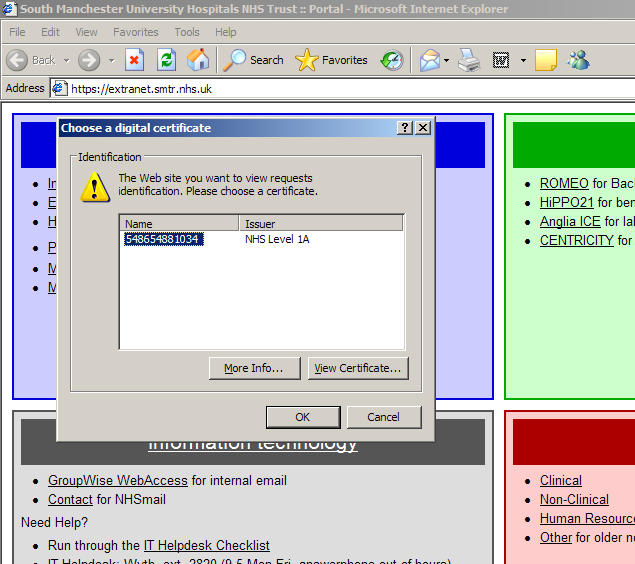
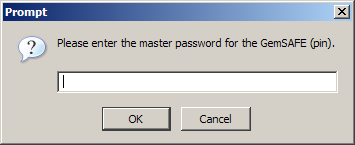
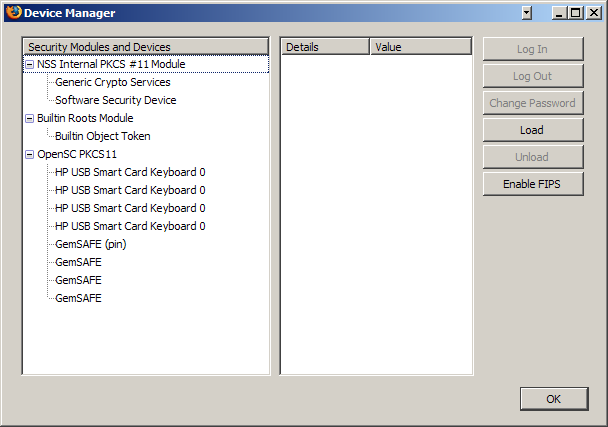
Use in Linux or in Mozilla on Windows
If you want to use the GemSAFE with Mozilla on Windows, you'll still
need OpenSC, and you'll still need to patch your opensc.conf
file. Then you can load the opensc-pkcs11.so or .dll module
into the browser. The OpenSC project has step-by-step instructions
for installing OpenSC into Mozilla.
Caveats
Sadly, the NHS smartcard's certificate does not necessarily carry any identifying information (the print on the card does, however, carry my photograph and my name). Here is a dump of most of the information on one of my cards:
maz@paradigmshift:~$ pkcs15-tool -r 01 | openssl x509 -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1086704611 (0x40c5cbe3)
Signature Algorithm: sha1WithRSAEncryption
Issuer: O=nhs, OU=CA, CN=NHS Level 1A
Validity
Not Before: Nov 22 10:05:10 2005 GMT
Not After : Nov 22 10:35:10 2007 GMT
Subject: O=nhs, OU=People, CN=548654881034
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
...long hex-encoded string here...
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage:
Digital Signature
X509v3 Private Key Usage Period:
...as above...
X509v3 Certificate Policies:
Policy: 1.2.826.0.1275.101.0.3.1.1
X509v3 CRL Distribution Points:
DirName:/O=nhs/OU=CA/CN=NHS Level 1A/CN=CRL241
X509v3 Authority Key Identifier:
keyid:3D:BD:89:00:DD:18:65:A0:7F:07:A5:B5:30:DA:34:11:2A:7C:B7:F8
X509v3 Subject Key Identifier:
1F:2C:35:14:F6:4B:AE:6A:0B:B0:35:BF:E4:E2:DE:D7:4C:D1:A9:F2
X509v3 Basic Constraints:
CA:FALSE
1.2.840.113533.7.65.0:
0
..V7.1....
Signature Algorithm: sha1WithRSAEncryption
...long hex-encoded string here...
Compare and contrast with the other card:
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1107903350 (0x42094376)
Signature Algorithm: sha1WithRSAEncryption
Issuer: O=nhs, OU=CA, CN=NHS Level 1B
Validity
Not Before: Nov 17 13:10:16 2005 GMT
Not After : Nov 17 13:40:16 2007 GMT
Subject: O=nhs, OU=People, CN=548654881034_Marek_Isalski
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
...different hex-encoded string...
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Non Repudiation
X509v3 Private Key Usage Period:
...as above...
X509v3 Certificate Policies: critical
Policy: 1.2.826.0.1275.102.0.3.2.0
CPS: ...long NHS-only URL...
X509v3 CRL Distribution Points:
DirName:/O=nhs/OU=CA/CN=NHS Level 1B/CN=CRL215
X509v3 Authority Key Identifier:
keyid:00:6C:AF:AD:CE:46:A6:9F:01:2C:76:8A:0F:1F:90:76:D9:74:05:86
X509v3 Subject Key Identifier:
6A:38:6E:F0:43:B3:DB:2F:6E:09:D3:78:C6:BA:D8:82:30:14:2B:07
X509v3 Basic Constraints:
CA:FALSE
1.2.840.113533.7.65.0:
0
..V7.1....
Signature Algorithm: sha1WithRSAEncryption
...different hex-encoded string...
The DNs are different, even though the card is issued to the same person.
The number part of the DN corresponds to the number printed on the front of the card.
Different CAs!
It seems to be the case that there are two User CAs in the NHS, called 1A and 1B. The default NPfIT/NHS smartcard toolkit I was provided with only had an installable certificate for one of the two CAs. I now have two NHS smartcards: one signed by each user CA. Bear this in mind when setting up your server's CA chain!
Different public keys (presumably the private key has been generated by the smartcard, rather than chosen by the enterprise CA software from Gemplus).
The URL for the content-commitment policy is restricted to NHS users (not accessible outside NHSnet/N3). If you were wondering what secrets lie behind this URL, fear not for all is revealed:
Our apologies... The item you requested does not exist on this server or cannot be served.
